Gaara Vulnhub/Proving grounds CTF Lab walkthrough

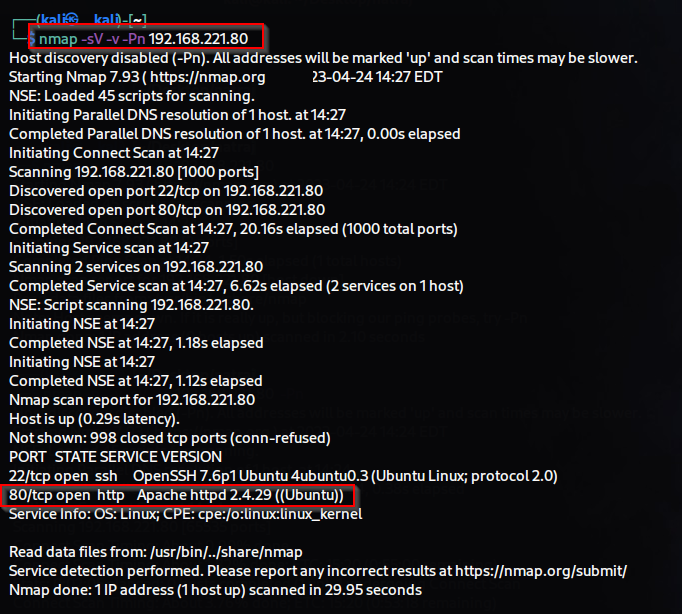
Welcome to my blog! 😊 Hello, friends, My name is Ajay I am a cybersecurity analyst. Gaara: The Gaara lab contains multiple vulnerabilities that allow attackers to gain unauthorized access to the system and escalate privileges. The lab is designed to be challenging, and users are required to use various tools and techniques to identify and exploit the vulnerabilities. It is important to note that the use of the Gaara lab should only be for educational and learning purposes, and not for any malicious activities. It is recommended that users have a basic understanding of networking, Linux, and ethical hacking before attempting to use the lab. In today's lab, we will be utilizing new techniques and methodologies in penetration testing. In this lab, we will be following these steps: Information gathering using nmap. Directory brute-forcing SSH Password Brute-forcing Using Hydra Privilege escalation by SUID Bit Set on gdb Step 1:- ...