EVILBOX Vulnhub/Proving grounds CTF Lab walkthrough
Welcome to my blog! 😊
Hello, friends, My name is Ajay I am a cybersecurity analyst.
EVILBOX:
In today's lab, we will be utilizing new techniques and methodologies in penetration testing. In this lab, we will be following these steps:
- Information gathering using nmap.
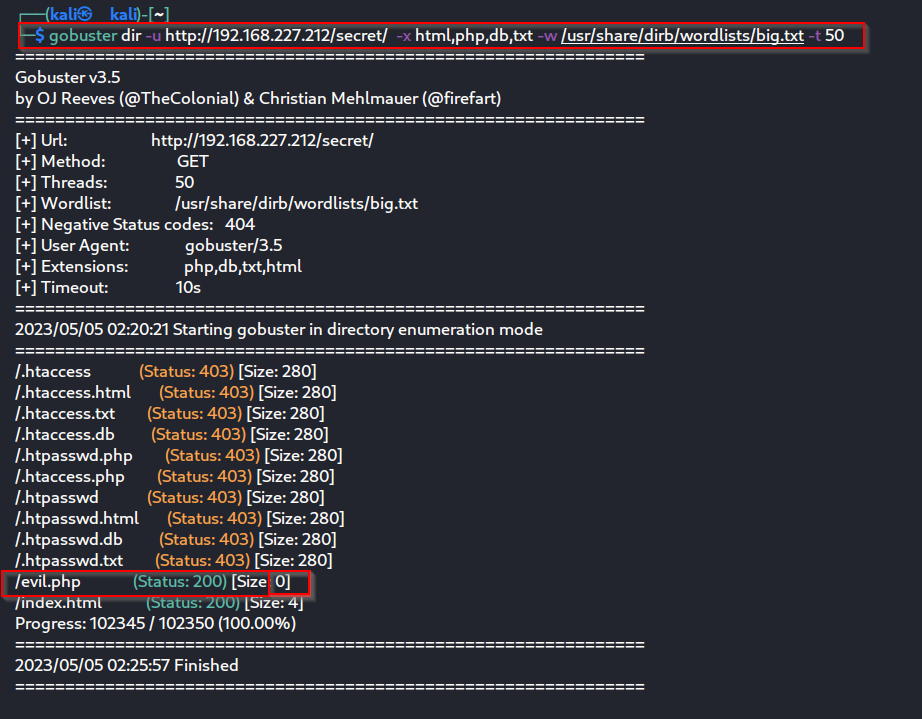
- Directory brute-forcing .
- LFI (Local File Inclusion) exploitation using fuff.
- Obtaining the public key of a user through SSH.
- Extracting the passphrase from an SSH key.
- Creating a hash using the SSH key.
- Cracking the hash using John the Ripper.
- Privilege escalation by editing the /etc/passwd file.
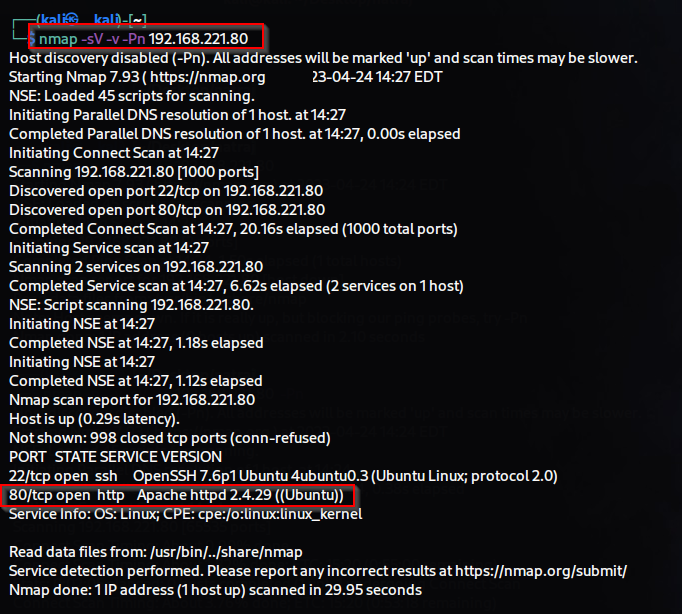
Step 1:- Scanning
--script=vuln option. Here is the output I obtained:In the "/robots.txt" file, we found the entry "Hello H4x0r." We have made a note of it as it may be relevant for future reference.
When I accessed "/secret/", I found that it was blank or empty. There was no content or information available in that directory.
Step 2 :- Enumeration
If I come across a file with the .php extension, as an experienced hacker, I should consider attempting to find Local File Inclusion (LFI) vulnerabilities. To accomplish this, I utilized the ffuf tool to perform brute-forcing specifically for LFI.
ffuf tool is a versatile and powerful command-line tool
used for fuzzing and discovering hidden content or potential
vulnerabilities in web applications. It stands for "Fuzz Faster U Fool"
and is designed to be fast, flexible, and easy to use. Here are some
common use cases for ffuf.Step 3 :- Gaining System Access
After identifying the LFI vulnerability, I attempted to extract the target system's ssh public key using the LFI technique.
id_rsa to 700 and proceed with the SSH login.As soon as I attempted to log in as the "mowree" user using the SSH public key, it prompted me to enter the passphrase for authentication.
A passphrase is an additional layer of security used to protect an SSH private key. It is a passphrase that is associated with the private key and is used to encrypt and decrypt the key when it is used for authentication.
To find the passphrase key for the use of id_rsa file, we will use the ssh2john tool.
ssh2john is a tool that is used to extract the passphrase hash from an SSH private key file, which can then be cracked using password cracking tools like John the Ripper. It converts the private key file format into a format that is compatible with John the Ripper, a popular password cracking tool.
$ ssh2johhn -d_rsa >file_name ( i am using hash as a file name)
After obtaining the passphrase hash, we proceeded to crack it using the John the Ripper tool.
Congratulations, we successfully cracked the hash!😏😏
$ john --wordlist=/home/kali/Desktop/rockyou.txt hash
Now, we have successfully logged in using the SSH public key and passphrase. Congratulations! You have obtained the "local.txt" flag.
$ ssh mowree@target-ip -i id_rsa
id (for see uid & gid etc. )
ls (for list the content )
cat local.txt (for read the file content )
Now, we will check for privilege escalation using the "lse.sh" script.
Having write permission on the "/etc/passwd" file is considered a vulnerability because it allows any user on the system to modify the contents of the file. The "/etc/passwd" file contains essential user account information, such as usernames, user IDs, home directories, and login shells. If an attacker gains write access to this file, they can potentially modify user account details, escalate privileges, or create malicious user accounts
cat command to print the contents of the "/etc/passwd" file on the terminal, and we copied the contents.Then, I generated the hash for a password using the mkpasswd tool. I used the password "1234" and generated its hash using the SHA-512 algorithm.
$ mkpasswd -m sha-512 (for create a password hash)
then i copied the hash
Then, we created a file named "passwd" using a text editor and pasted the content of "/etc/passwd" into it. Additionally, I added a user named "anytimehack" by appending the following line to the file
After adding the user and modifying the "passwd" file, I saved the file to the path of a Python server.
Now, using the "su" command, we will access the "anytimehack" user account. for gain root access, Congratulations! Now You have root access, and you have obtained the "root.txt" flag.























Comments
Post a Comment